Ping Identity
This document covers configuring Ping Identity as an IdP for your Pomerium gateway. It assumes you have already installed Pomerium.
caution
While we do our best to keep our documentation up to date, changes to third-party systems are outside our control. Refer to Adding an application - Web application from Ping's documentation as needed, or let us know if we need to re-visit this page.
Create OpenID Connect App
To use the Ping Identity provider, first go to the Ping One console and select the environment you want to create the app for.
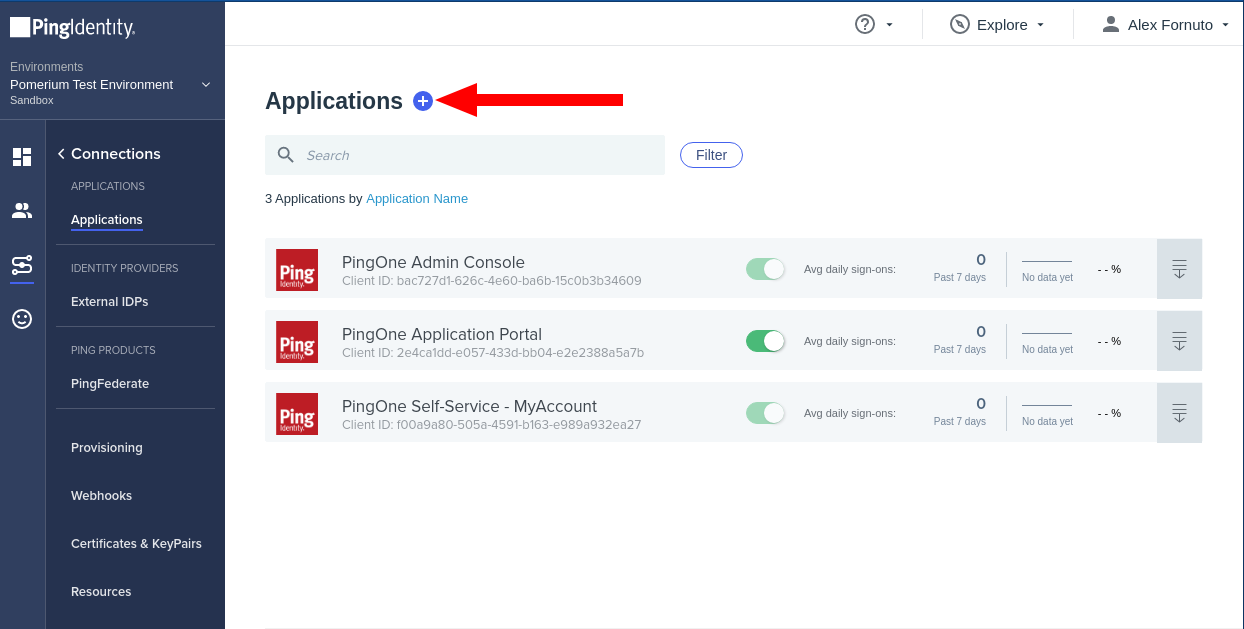
Click Connections in the side menu, select Applications and click + button to create a new application:
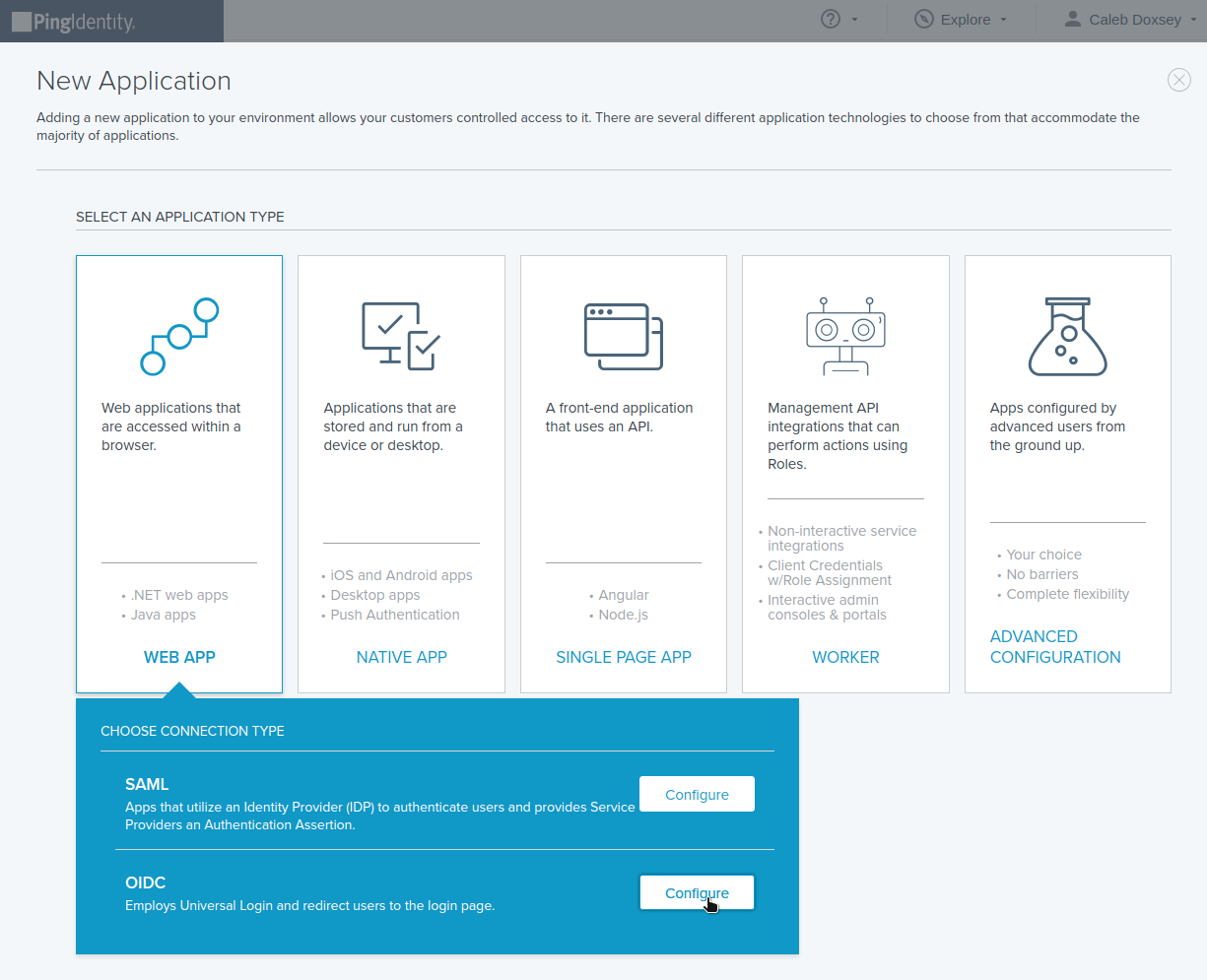
Select WEB APP, then OIDC:
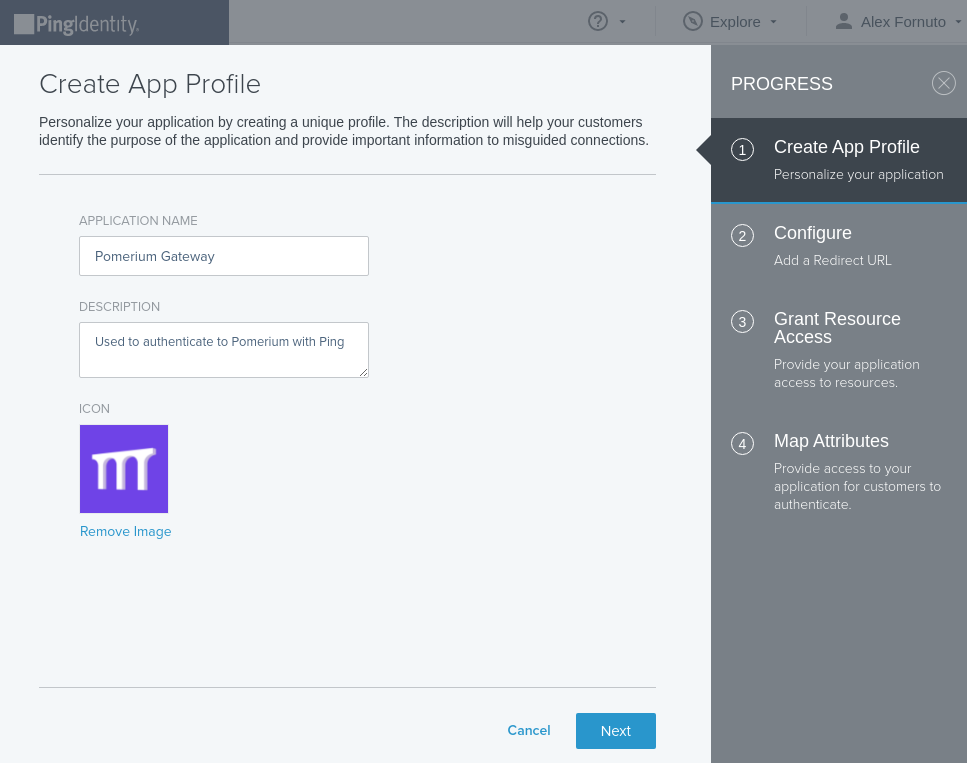
Name the application and optionally provide a description and icon:
On the Configure page, add the Pomerium authenticate redirect URL. For example:
https://authenticate.localhost.pomerium.io/oauth2/callback.Provide the necessary scopes to your application as needed for your policies from the scopes available in the OpenID Spec. Pomerium requires at least the
emailscope: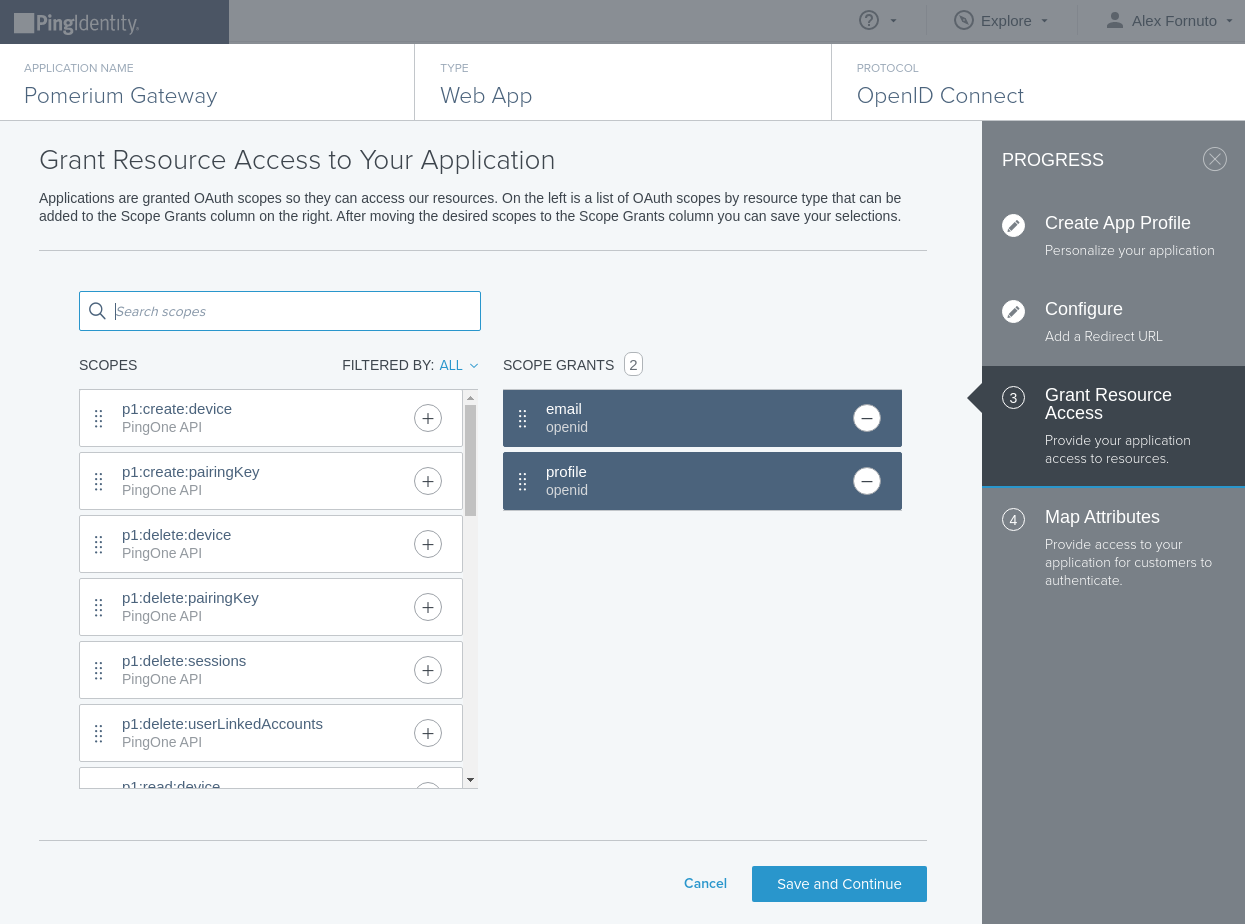
OIDC Attributes. Save and Close.
From the Configuration tab of your new application, note the values of the following keys to use in your Pomerium Configuration:
- ISSUER: used as the
idp_provider_url(e.g.https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as) - CLIENT ID: used as the
idp_client_id - CLIENT SECRET: used as the
idp_client_secret
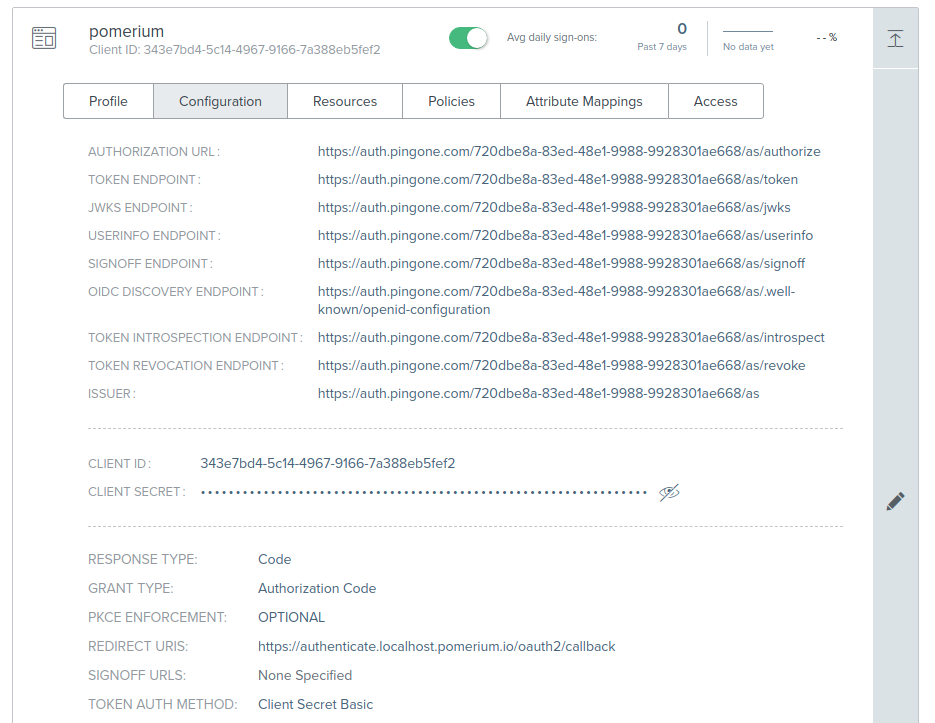
- ISSUER: used as the
Toggle the green slider to enable your new application.
Service Account
To use allowed_groups in a policy, an idp_service_account needs to be set in the Pomerium configuration. The service account for Ping uses a different application, and client ID and client secret from the one configured above.
Click Add Application, but this time select Worker → Worker App.
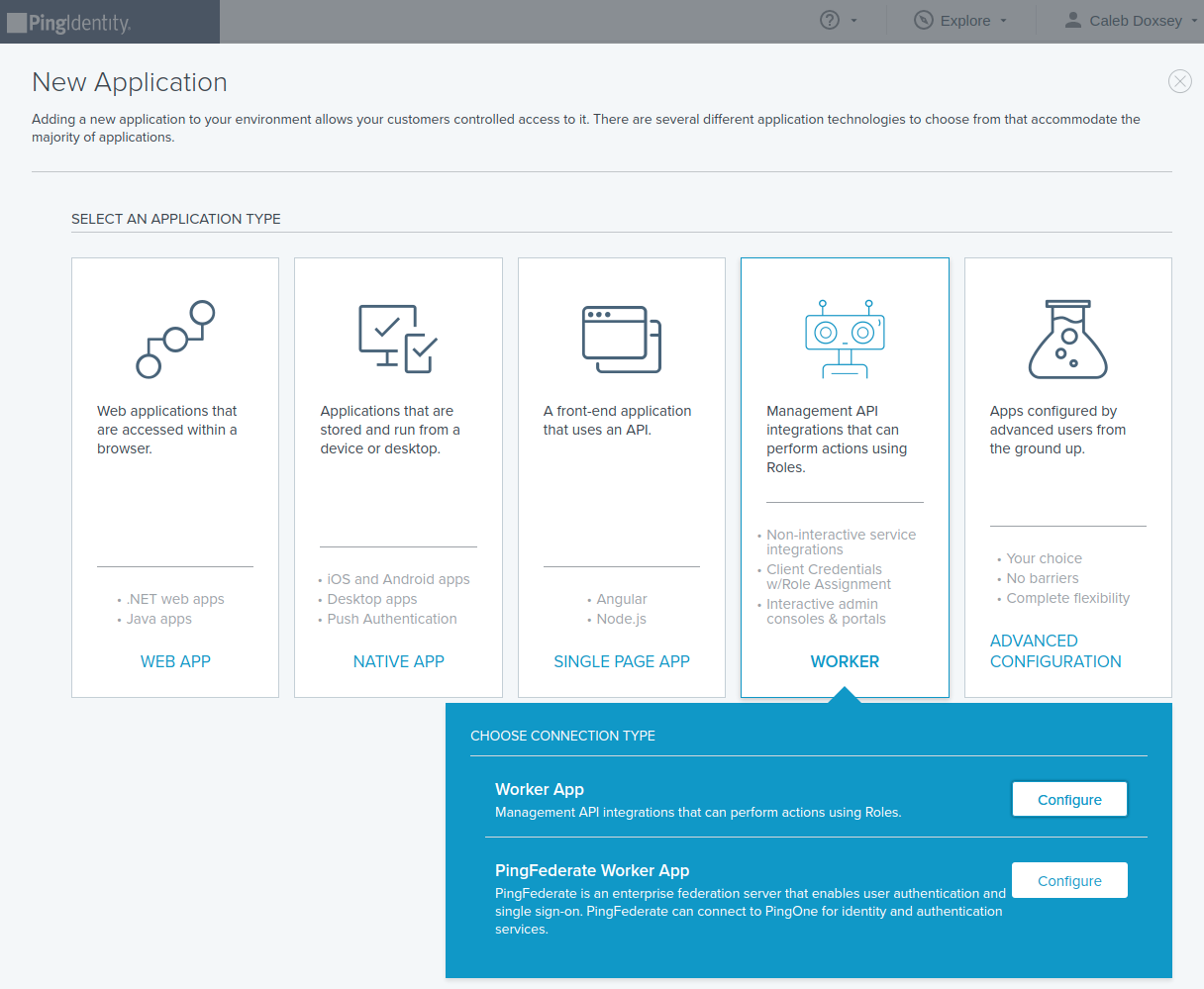
Toggle the green slider to enable your new application.
This application's Client ID and Client Secret will be used as the service account in Pomerium.
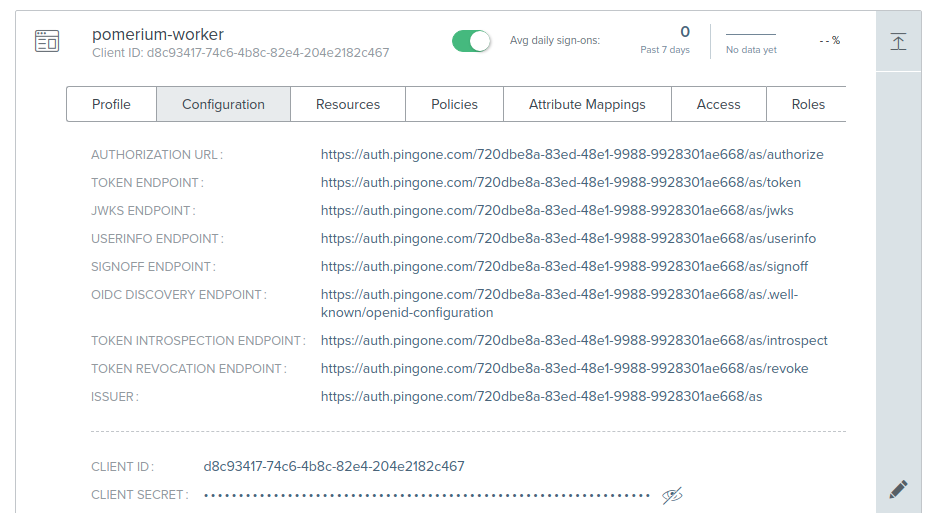
The format of the service account is a JSON encoded object with
client_idandclient_secretproperties:{
"client_id": "XXXXXXXXXX",
"client_secret": "XXXXXXXXXX"
}You can save the object as a temporary file to encode as a base64 value:
cat tmp.json | base64 -w 0
Pomerium Configuration
Update your Pomerium configuration to use Ping as the IdP:
- config.yaml
- Environment Variables
idp_provider: "ping"
idp_provider_url: "https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as"
idp_client_id: "CLIENT_ID"
idp_client_secret: "CLIENT_SECRET"
idp_service_account: "XXXXXXX" # Base64-encoded JSON
IDP_PROVIDER="ping"
IDP_PROVIDER_URL="https://auth.pingone.com/720dbe8a-83ed-48e1-9988-9928301ae668/as"
IDP_CLIENT_ID="CLIENT_ID"
IDP_CLIENT_SECRET="CLIENT_SECRET"
IDP_SERVICE_ACCOUNT="XXXXXXX" # Base64-encoded JSON