Pomerium using Docker
In this quick-start document, we'll create a minimal but complete environment for running Pomerium with containers.
Prerequisites
- A configured identity provider
- Docker and docker-compose
- TLS certificates
- This document assumes that your local Docker environment does not have a fully qualified domain name (FQDN) routed to it, and that you followed Self-signed wildcard certificate to generate a locally trusted key pair. Otherwise, adjust the configurations below to match your certificate solution.
Configure
Create a configuration file (e.g
config.yaml) for defining Pomerium's configuration settings, routes, and access policies. Consider the following example:# See detailed configuration settings : https://www.pomerium.com/docs/reference/
# this is the domain the identity provider will callback after a user authenticates
authenticate_service_url: https://authenticate.localhost.pomerium.io
####################################################################################
# Certificate settings: https://www.pomerium.com/docs/reference/certificates.html #
# The example below assumes a certificate and key file will be mounted to a volume #
# available to the Docker image. #
####################################################################################
certificate_file: /pomerium/cert.pem
certificate_key_file: /pomerium/privkey.pem
##################################################################################
# Identity provider settings : https://www.pomerium.com/docs/identity-providers/ #
# The keys required in this section vary depending on your IdP. See the #
# appropriate docs for your IdP to configure Pomerium accordingly. #
##################################################################################
idp_provider: google
idp_client_id: REPLACE_ME
idp_client_secret: REPLACE_ME
#idp_service_account: REPLACE_ME # Required by some identity providers for directory sync
# Generate 256 bit random keys e.g. `head -c32 /dev/urandom | base64`
cookie_secret: V2JBZk0zWGtsL29UcFUvWjVDWWQ2UHExNXJ0b2VhcDI=
# https://pomerium.com/reference/#routes
routes:
- from: https://verify.localhost.pomerium.io
to: http://verify:8000
policy:
- allow:
or:
- email:
is: user@example.com
pass_identity_headers: trueKeep track of the path to this file, relative to the
docker-compose.ymlfile created in the next step.docker-compose.ymlwill need the correct relative path to yourconfig.yaml.Create or copy the following
docker-compose.ymlfile and modify it to match your configuration, including the correct paths to yourconfig.yamland certificate files:version: "3"
services:
pomerium:
image: pomerium/pomerium:latest
volumes:
## Mount your domain's certificates : https://www.pomerium.com/docs/reference/certificates
- ./_wildcard.localhost.pomerium.io.pem:/pomerium/cert.pem:ro
- ./_wildcard.localhost.pomerium.io-key.pem:/pomerium/privkey.pem:ro
## Mount your config file : https://www.pomerium.com/docs/reference/
- ./config.yaml:/pomerium/config.yaml:ro
ports:
- 443:443
## https://verify.localhost.pomerium.io --> Pomerium --> http://verify
verify:
image: pomerium/verify:latest
expose:
- 8000
Run
Run docker compose:
docker-compose up
Docker will automatically download the required container images for Pomerium and verify. Then, Pomerium will run with the configuration details set in the previous steps.
You should now be able access to the routes (e.g. https://verify.localhost.pomerium.io) as specified in your policy file.
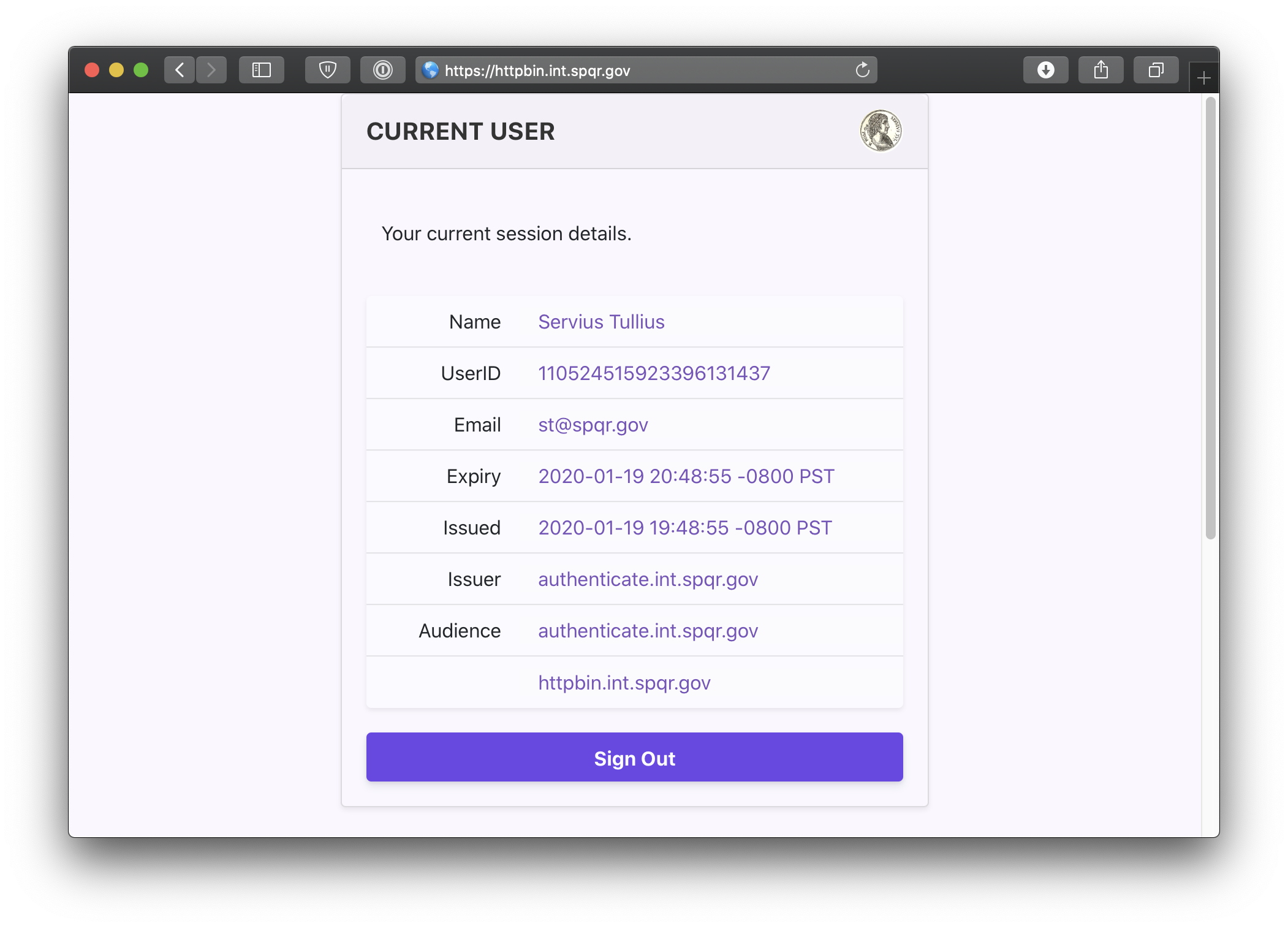
You can also navigate to the special pomerium endpoint verify.localhost.pomerium.io/.pomerium/ to see your current user details.
Next Steps
Now you can experiment with adding services to Docker and defining routes and policies for them in Pomerium. See Guides for help or inspiration.
This is a test environment!
If you followed all the steps in this doc your Pomerium environment is not using trusted certificates. Remember to use a valid certificate solution before moving this configuration to a production environment. See Certificates for more information.